Features
Diva is aiming to become the most decentralized & resilient staking solution, offering the best features to both Stakers and Operators.
There are three ways to engage with Diva Staking:
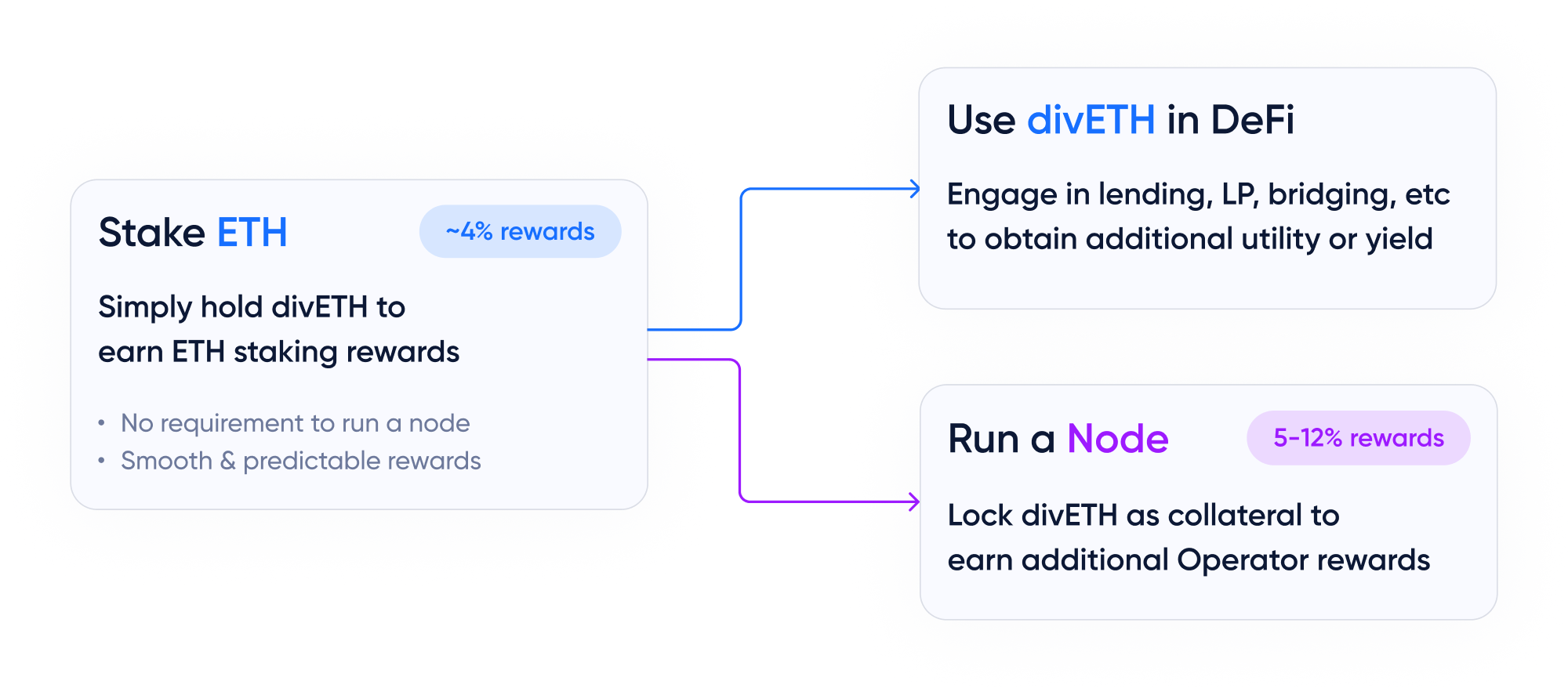
💧 Liquid Staking
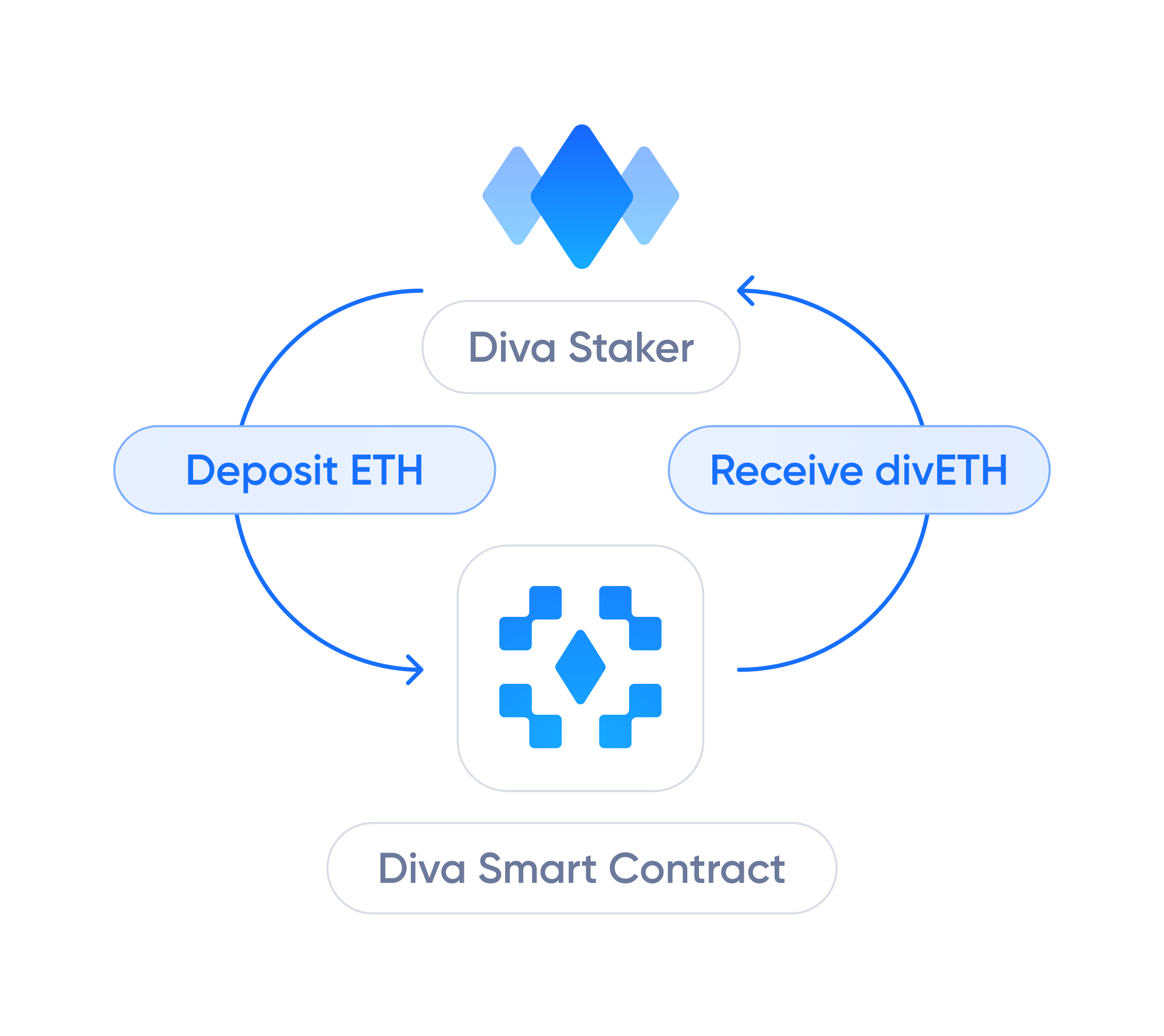
Diva Staking allows Liquid Stakers to generate staking rewards without having to lock their ETH.
Liquid Stakers simply need to hold their divETH to generate Staking Rewards, and can also use it in DeFi for things like lending, bridging, etc.
This provides a model with many advantages Ethereum's native staking, which requires locking 32Ξ without liquidity and operating hardware.
Learn more about Diva's Liquid Staking.
🔒 Non-custodial
Operators never have access to user funds. Diva Staking automatically stakes all ETH deposited, by depositing it into Ethereum validators.
Further, Operators never have access to full validator keys and are unable to unilaterally request the withdrawal of funds from validators.
🤝 Staker Protection
Staking is risky, because if Operators are offline or malicious, Stakers can face partial or full loss of ETH funds.
In Diva, Stakers are protected against losses because Operators provide collateral which is pledged to Stakers to compensate potential losses.
💠 Distributed Validators

Diva Staking uses its own DVT to deliver superior performance and risk management.
All validator actions require a consensus signature of 2/3rds of nodes in the committee, making Diva resistant to collusion attacks.
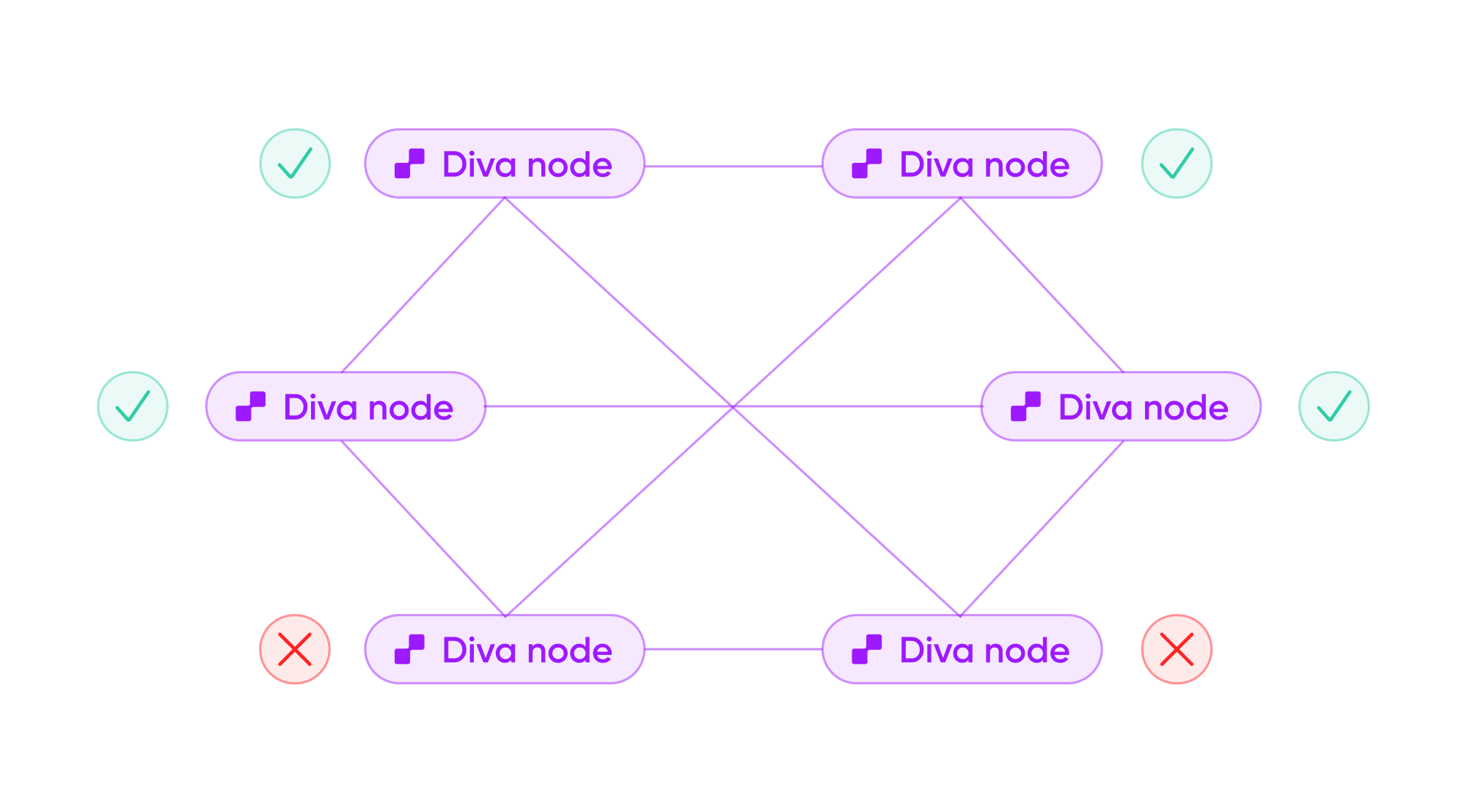
Key-shares are generated using Multi-Party Computation (MPC) so secret keys never come together. This greatly reduces the risk of hacks or loss of private keys.
👨👩👧👦 Permissionless
Diva allows anybody to stake ETH or operate a node without requiring any kind of approvals or permissions.
🌎 Decentralized
Every Diva validator is a Distributed Validator, operated by a stochastically distributed sub-network of nodes.
Diva has built-in Sybil protection mechanisms and is focused on reducing the barriers to entry for Operators, promoting diversity and true decentralization.
🌳 Resilient

Thanks to the properties of Diva's validator sets, only 2/3rds ("n of m") signatures are needed to reconstruct the total signature representing the private key for each validator.
Consequently, Diva validators tolerate up to "m - n" failing nodes, and the validation will not be affected in case of partial validation failure.
This makes Diva resilient to periods of node unavailability, even when multiple nodes go offline, and allows safety mechanisms to safely regenerate DKG and recover network liveliness.
🚅 Efficient networking
Diva uses a P2P network for node discovery. Communications occur directly between peers without the need for a "Diva blockchain".
👀 Trust-minimized
Diva is being designed to minimize the trust required from any party, providing:
- A strong cryptographic model to protect staking operations.
- ETH collateral as protection towards potential losses.
- Zero-knowledge mathematical proofs for reports and calculations.
💬 Censorship-resistant
The architecture of the Diva Staking Protocol has been designed to be censorship-resistant, in line with Ethereum's community values.
💠 An extension of Ethereum
Ultimately, the Diva Staking Protocol acts as a software extension of Ethereum, providing permissionless mechanisms to perform staking in a more efficient and decentralized way.